Containerization
Containerization is a method of deploying an application or computing service in microseconds in its own encapsulated environment, a “container”. Rather than loading an application or service onto an entire machine with an operating system and associated overhead, a “container” has its own environment that hosts the application, its required operating system, and specific resources. Due to its agile nature, Containerization is favored to be used in cloud environments, but can also be implemented on virtual machines (VMs) as well as physical devices. The advantage of using containers is that they can be instantiated at a rapid speed and that they only use the minimal resources associated with running the application or service they support.
Mission Impact
- Deploy applications quickly, reliably and consistently regardless of environment
- Increase developer productivity by removing cross-service dependencies and conflicts
- Improve resource utilization
- Provide process isolation and improve security
- Simplify automation in DevOps environments
Features
- Flexible implementation options (SaaS, On-Premise, Hybrid)
- Environment Consistency (Development, Test, Production)
- Operational Efficiency
- Track versions of application code and their dependencies
Use Cases
- Organizations looking to create distributed applications by breaking apart applications into independent tasks or processes (e.g., microservices) and deploying them into containers
- Organizations implementing batch and “extract, transform, load” (ETL) jobs by packaging the job into a container and deploying it into a shared cluster
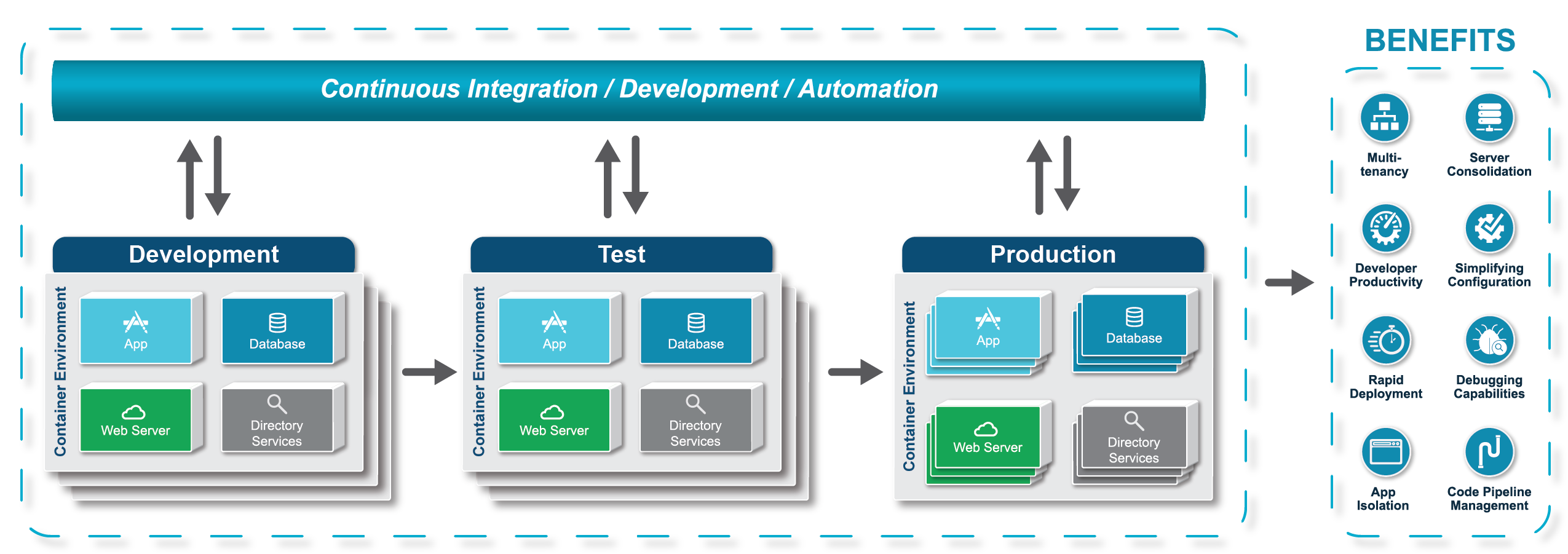
- Organizations looking to improve their continuous integration and deployment processes by packaging applications into containers and moving them through the development, testing and production environments
Infographic
Considerations
- A consistent process to build images needs to be developed, and image repositories need to be created.
- Although most containers are isolated from the risk of network intrusion and various attack vectors common to production servers, there is still a need for network traffic monitoring and security patching.
- DNS and Load Balancing strategies need to be taken into account when deploying containers.
- As applications mature and traffic increases, rolling upgrades or blue-green deployment strategies will need to be used to prevent site outages.
- The production infrastructure will require support for log aggregation across containers.
ValidaTek's Process
- Provide enterprise security consulting guidance
- Identify use cases and primary users
- Examine current IT operational environment and toolset to include:
a. Storage, Network, and Compute Resources
b. Types of tools (Monitoring, Orchestration, Automation.) - Define success criteria in measurable terms
a. Key Performance Indicators (KPIs)
b. Return on Investment (ROI) - Identify core challenges that could be solved through the use of containers
a. Application portability
b. Resource Utilization
c. DevOps - Evaluate container platforms and provide recommendations based on analysis of the current environment, challenges, and success criteria.
- Engineer and architect Container solutions
- Integrate, test, and implement container environments and solutions with existing IT infrastructures or Cloud services.
For More Information
Email: [email protected]
Phone: 703-972-2272




